Cryptography has many different ways of functioning. Before you can understand the
basic process, you must become familiar with some terminology. With this in mind, let’s
look at a few of the main terms used in the field of cryptography:
Plain Text/Clear Text Plain text is the original message. It has not been altered; it is
the usable information. Remember that even though Caesar’s cipher operates on text, it is
but one form of plain text. Plain text can literally be anything.
Cipher Text Cipher text is the opposite of plain text; it is a message or other data that
has been transformed into a different format using a mechanism known as an algorithm.
It is also something that can be reversed using an algorithm and a key.
Algorithms Ciphers, the algorithms for transforming clear text into cipher text, are the
trickiest and most mysterious part of the encryption process. This component sounds
complex, but the algorithm or cipher is nothing more than a formula that includes
discrete steps that describe how the encryption and decryption process is to be performed
in a given instance.
Keys Keys are an important, and frequently complicated, item. A key is a discrete piece of
information, usually random in nature, that determines the result or output of a given
cryptographic operation. A key in the cryptographic sense can be thought of in the same
way a key in the physical world is: as a special item used to open or unlock something—in
this case, a piece of information. In the encryption world, a key is used to produce a
meaningful result and without it a result would not be possible.
The terms listed here are critical to understanding all forms of cryptography.
You’ll be seeing them again not only in this chapter but in later chapters as well. In
addition, a firm understanding of cryptography will go far in giving you a head start
in understanding many security technologies and concepts outside of the CEH exam.
Next, let’s look at the two major types of cryptography: symmetric and asymmetric (aka
public-key cryptography).
Symmetric Cryptography
Symmetric algorithms do some things really well and other things not so well. Modern
symmetric algorithms are great at all of the following:
Preserving confidentiality
Increased speed over many non-symmetric systems
Ensuring simplicity (relatively speaking, of course)
Providing authenticity
Symmetric algorithms have drawbacks in these areas:
Key management issues
Lack of nonrepudiation features
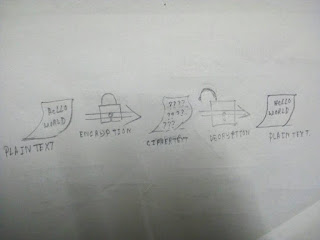
First, let’s focus on the defining characteristic of symmetric encryption algorithms: the
key. All algorithms that fit into the symmetric variety use a single key to both encrypt and
decrypt (hence the name symmetric). This is an easy concept to grasp if you think of a key
used to lock a gym locker as the same key used to unlock it. A symmetric algorithm works
exactly the same way: The key used to encrypt is the same one used to decrypt. Figure 3.2
shows the concept of symmetric encryption.
Figure 3.2 Symmetric encryption
Common Symmetric Algorithms
There are currently a myriad of symmetric algorithms available to you; a Google search
turns up an endless sea of alphabet soup of algorithms. Let’s look at some common
algorithms in the symmetric category:
Data Encryption Standard (DES) Originally adopted by the U.S. Government in 1977,
the DES algorithm is still in use today. DES is a 56-bit key algorithm, but the key is too
short to be used today for any serious security applications.
DES is still encountered in many applications but should never be chosen without very
careful consideration or the lack of other viable options.
Triple DES (3DES) This algorithm is an extension of the DES algorithm and is three
times more powerful than the DES algorithm. The algorithm uses a 168-bit key.
Triple DES, or 3DES, is very commonly used and is a component of many security
solutions including e-commerce and others.
Blowfish Blowfish is an algorithm that was designed to be strong, fast, and simple in its
design. The algorithm uses a 448-bit key and is optimized for use in today’s 32- and 64-bit
processors (which its predecessor DES was not). The algorithm was designed by
encryption expert Bruce Schneier.
International Data Encryption Algorithm (IDEA) Designed in Switzerland and
made available in 1990, this algorithm is seen in applications such as the Pretty Good
Privacy (PGP) system (see the section “Pretty Good Privacy” later in this chapter).
The goal of the Advanced Encryption Standard (AES) competition,
announced in 1997, was to specify “an unclassified, publicly disclosed encryption
algorithm capable of protecting sensitive government information well into the next
century”
FIG- Symmetric encryption
The National Institute of Standards and Technology (NIST) organized the AES competition.
RC2 Originally an algorithm that was a trade secret of RSA Labs, the RC2 algorithm crept
into the public space in 1996. The algorithm allows keys between 1 and 2,048 bits. The
RC2 key length was traditionally limited to 40 bits in software that was exported to allow
for decryption by the U.S. National Security Agency.
RC4 Another algorithm that was originally a trade secret of RSA Labs, RC4, was revealed
to the public via a newsgroup posting in 1994. The algorithm allows keys between 1 and
2,048 bits.
RC4 is notable for its inclusion in the Wired Equivalent Protection (WEP) protocol used
in early wireless networks.
RC5 Similar to RC2 and RC4, RC5 allows users to define a key length.
RC6 RC6 is another AES finalist developed by RSA Labs and supports key lengths of 128–
256 bits.
Rijndael or Advanced Encryption Standard (AES) This successor to DES was
chosen by the National Institute of Standards and Technology (NIST) to be the new U.S.
encryption standard. The algorithm is very compact and fast and can use keys that are
128-, 192-, or 256-bits long.
Rijndael was and is the name of the encryption algorithm submitted for consideration by
the U.S. Government as its new encryption standard. When the algorithm was selected, it
was renamed AES. While some may argue that Rijndael and AES are different, they are
for all intents and purposes the same.
Twofish This AES candidate, also developed by Bruce Schneier, supports key lengths of
128–256 bits.
basic process, you must become familiar with some terminology. With this in mind, let’s
look at a few of the main terms used in the field of cryptography:
Plain Text/Clear Text Plain text is the original message. It has not been altered; it is
the usable information. Remember that even though Caesar’s cipher operates on text, it is
but one form of plain text. Plain text can literally be anything.
Cipher Text Cipher text is the opposite of plain text; it is a message or other data that
has been transformed into a different format using a mechanism known as an algorithm.
It is also something that can be reversed using an algorithm and a key.
Algorithms Ciphers, the algorithms for transforming clear text into cipher text, are the
trickiest and most mysterious part of the encryption process. This component sounds
complex, but the algorithm or cipher is nothing more than a formula that includes
discrete steps that describe how the encryption and decryption process is to be performed
in a given instance.
Keys Keys are an important, and frequently complicated, item. A key is a discrete piece of
information, usually random in nature, that determines the result or output of a given
cryptographic operation. A key in the cryptographic sense can be thought of in the same
way a key in the physical world is: as a special item used to open or unlock something—in
this case, a piece of information. In the encryption world, a key is used to produce a
meaningful result and without it a result would not be possible.
The terms listed here are critical to understanding all forms of cryptography.
You’ll be seeing them again not only in this chapter but in later chapters as well. In
addition, a firm understanding of cryptography will go far in giving you a head start
in understanding many security technologies and concepts outside of the CEH exam.
Next, let’s look at the two major types of cryptography: symmetric and asymmetric (aka
public-key cryptography).
Symmetric Cryptography
Symmetric algorithms do some things really well and other things not so well. Modern
symmetric algorithms are great at all of the following:
Preserving confidentiality
Increased speed over many non-symmetric systems
Ensuring simplicity (relatively speaking, of course)
Providing authenticity
Symmetric algorithms have drawbacks in these areas:
Key management issues
Lack of nonrepudiation features
First, let’s focus on the defining characteristic of symmetric encryption algorithms: the
key. All algorithms that fit into the symmetric variety use a single key to both encrypt and
decrypt (hence the name symmetric). This is an easy concept to grasp if you think of a key
used to lock a gym locker as the same key used to unlock it. A symmetric algorithm works
exactly the same way: The key used to encrypt is the same one used to decrypt. Figure 3.2
shows the concept of symmetric encryption.
Figure 3.2 Symmetric encryption
Common Symmetric Algorithms
There are currently a myriad of symmetric algorithms available to you; a Google search
turns up an endless sea of alphabet soup of algorithms. Let’s look at some common
algorithms in the symmetric category:
Data Encryption Standard (DES) Originally adopted by the U.S. Government in 1977,
the DES algorithm is still in use today. DES is a 56-bit key algorithm, but the key is too
short to be used today for any serious security applications.
DES is still encountered in many applications but should never be chosen without very
careful consideration or the lack of other viable options.
Triple DES (3DES) This algorithm is an extension of the DES algorithm and is three
times more powerful than the DES algorithm. The algorithm uses a 168-bit key.
Triple DES, or 3DES, is very commonly used and is a component of many security
solutions including e-commerce and others.
Blowfish Blowfish is an algorithm that was designed to be strong, fast, and simple in its
design. The algorithm uses a 448-bit key and is optimized for use in today’s 32- and 64-bit
processors (which its predecessor DES was not). The algorithm was designed by
encryption expert Bruce Schneier.
International Data Encryption Algorithm (IDEA) Designed in Switzerland and
made available in 1990, this algorithm is seen in applications such as the Pretty Good
Privacy (PGP) system (see the section “Pretty Good Privacy” later in this chapter).
The goal of the Advanced Encryption Standard (AES) competition,
announced in 1997, was to specify “an unclassified, publicly disclosed encryption
algorithm capable of protecting sensitive government information well into the next
century”
FIG- Symmetric encryption
The National Institute of Standards and Technology (NIST) organized the AES competition.
RC2 Originally an algorithm that was a trade secret of RSA Labs, the RC2 algorithm crept
into the public space in 1996. The algorithm allows keys between 1 and 2,048 bits. The
RC2 key length was traditionally limited to 40 bits in software that was exported to allow
for decryption by the U.S. National Security Agency.
RC4 Another algorithm that was originally a trade secret of RSA Labs, RC4, was revealed
to the public via a newsgroup posting in 1994. The algorithm allows keys between 1 and
2,048 bits.
RC4 is notable for its inclusion in the Wired Equivalent Protection (WEP) protocol used
in early wireless networks.
RC5 Similar to RC2 and RC4, RC5 allows users to define a key length.
RC6 RC6 is another AES finalist developed by RSA Labs and supports key lengths of 128–
256 bits.
Rijndael or Advanced Encryption Standard (AES) This successor to DES was
chosen by the National Institute of Standards and Technology (NIST) to be the new U.S.
encryption standard. The algorithm is very compact and fast and can use keys that are
128-, 192-, or 256-bits long.
Rijndael was and is the name of the encryption algorithm submitted for consideration by
the U.S. Government as its new encryption standard. When the algorithm was selected, it
was renamed AES. While some may argue that Rijndael and AES are different, they are
for all intents and purposes the same.
Twofish This AES candidate, also developed by Bruce Schneier, supports key lengths of
128–256 bits.